Git BFG Examples for Removal of Secrets
Published
Updated
Sometimes you may commit a file or accidentally push data into remote which contains sensitive information. Passwords, private keys, personal information, etc. can be easily removed from Git and the repository history using the BFG repo cleaner utility. The following steps outline how to remove any sensitive information from your repository as well as the history, all without deleting any unnecessary data or files.
Installing BFG
The easiest way to install BFG is to use homebrew. Install it by running the following command, or alternatively download the jar from the project site.
brew install bfg
Preparing your Remote Repository
In order to overwrite the history across the entire repository, you need to make a few tweaks to make sure the new (clean) history can be force-pushed.
- Make sure to close any open pull requests that are pointing to the remote repository
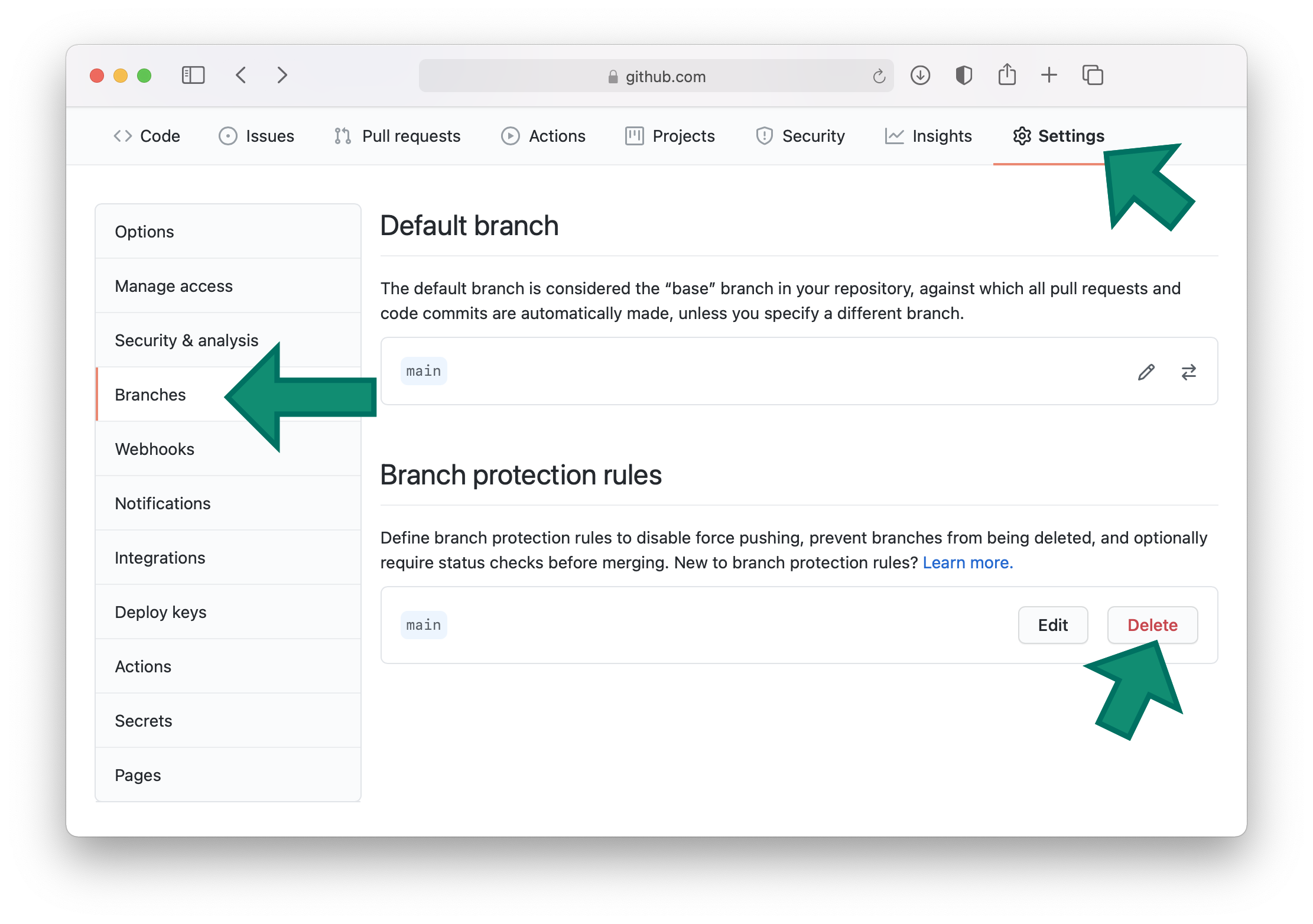
- Temporarily disable any branch protection rules that may exist
You can remove branch protection rules within the branches tab located within the repository settings at Github (see below).
Procedure for Removing Sensitive Data
The following steps will allow you to clone a copy of the affected repository, delete / replace any sensitive data, overwrite the history, and replace the remote repo’s history.
1 - Clone the affected repository
mkdir my-repo-clean
cd my-repo-clean
git clone --mirror https://github.com/myrepo/myrepo.git
2 - Delete or replace any sensitive files
If you wish to delete the file entirely, run the following:
bfg --delete-files myprivatekey.pem
If the remote file has already had the sensitive data removed, but the history still needs to be scrubbed, run the following instead:
bfg --replace-text myscrubbedfile.properties
3 - Rewrite the history and Push to Remote
The following commands will overwrite the commit history and forcefully push the changes to your remote repository - updating all tags and branches.
git reflog expire --expire=now --all && git gc --prune=now --aggresive
git push -f
Note: If you receive any errors like remote rejected you can ignore these. I think they are for historical read-only pull requests which have histories that cannot be overridden.
4 - Clean up
- Ensure any other team members delete the local copies of the repository and re-clone it from remote.
- Restore any branch protection rules that were previously deleted or disabled.
